Scope for Cybersecurity in 2024 - Update for 2024
-
 By Sushmith
By Sushmith - Published on Dec 20 2024

Introduction to Cybersecurity
What is cybersecurity? Cybersecurity is the process of implementing methods to protect against unauthorized access and related cyber-attacks and threats.
The Future of Cybersecurity completely relies on the current state and the balance between security, privacy, and other confidential information.
Cybersecurity helps maintaining confidential businesses information secured. This helps businesses provide good services to their customers and maintain quality in their products.
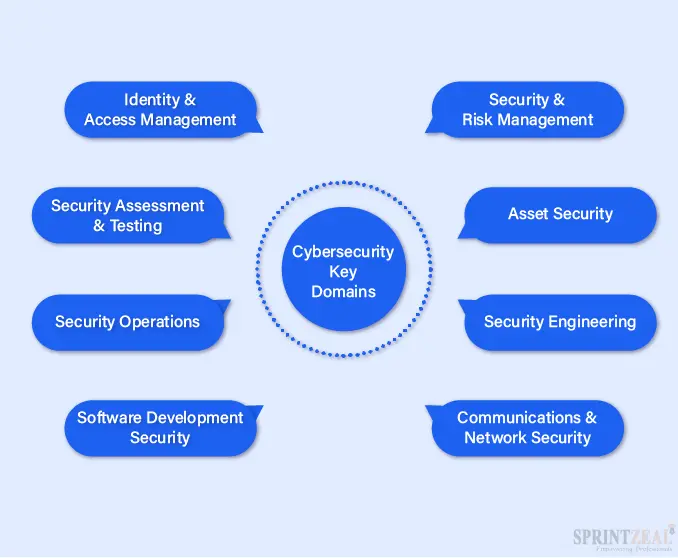
Cybersecurity protects the confidential assets of an organization. Application security, network security, cloud security, and other such sub-domains make up cybersecurity.
Table of Contents
Future risks in Cybersecurity
It is said that, by the year 2025, 80% of organizations will begin to adapt methods to merge web services and cloud services from a single service edge. By 2030, 80% of organizations will begin to use cybersecurity risks in business transactions and third-party transactions as a prime element.
Cybersecurity in 2024 would have a change in all the current trends, and the job scope would change as well. This would lead to a need for more cybersecurity data analysts.
In the following years, it is definite that there will be an increased risk of ransomware attacks. This places a significant toil on the organizations' security teams.
Importance of Cybersecurity
As the economic value of data increases, so do the threats to it. Since it is crucial to protect sensitive data that could pose a major threat, cybersecurity is very important. These threats make it very complicated for the organizations to handle the data breaching.
Maintaining a good reputation is very important to any organization in the market.
Even a small breach in the data can cause a great loss to the company's reputation. With this, it becomes very crucial for every organization to secure such data, both to avoid cyber threats and to maintain a good reputation.
Devices that are connected to public Wi-Fi are more vulnerable to any confidential information they contain. In any case, relying on systematic cybersecurity software tools aids in identifying operating system flaws.
Detection, or anticipating data breaches, assists individuals in remaining aware of data thefts.
Currently, data has become a much more valuable asset. This is because of all the details that can be decrypted and the knowledge they can provide. So, cybersecurity helps in securing such sensitive business data by securing the connected devices from cybercriminals.
Predictions of cybersecurity for 2024
What will cybersecurity look like in 2024?
With the current rates of cybercrime, by the end of 2024, there will be a critical need for data-centric security and privacy. With cybercrime costs projected to reach a staggering $10.5 trillion globally by 2025, securing user data would become one of the most prioritized assets for any organization. Here's what we can expect in the ever-evolving cybersecurity landscape of 2024:
- Data-Centric Security Takes Center Stage:
As data breaches continue to dominate headlines, securing user information will become paramount. Organizations will likely invest heavily in data loss prevention (DLP) solutions, cloud security measures, and robust identity and access management (IAM) protocols to safeguard sensitive data. - Privacy-Enhancing Technologies Emerge:
Technologies like homomorphic encryption and zero-knowledge proofs are gaining traction, allowing users to control their data while still enabling its utilization for analytics or other purposes. This shift towards privacy-preserving approaches will be crucial in building trust with users and complying with stricter data privacy regulations like GDPR and CCPA. - AI-Powered Security: A Double-Edged Sword:
Artificial intelligence (AI) will play a more prominent role in cybersecurity. AI-powered tools can be invaluable for threat detection, automation of security tasks, and faster incident response. However, it's crucial to be aware of the potential for AI to be misused by attackers as well. Robust security practices and the ethical development of AI tools will be critical in this domain.
Privacy-encrypting technologies would take the lead, because this would create a requirement for the users to protect their assets. By staying informed about these evolving trends and implementing proactive security measures, organizations can navigate the ever-changing cybersecurity landscape of 2024 and beyond.
Ransomware attacks have now begun to become more threatening since cybercriminals only continue to sharpen their skills and amplify their attacks. This leads to an imbalance in the market.
For the year 2024, here are some of the possible changes that are to be expected in the field of cybersecurity.
Cybersecurity predictions in 2024 (Suggested Read)
Career Path
One does not have to be qualified from the MIT to work in cybersecurity. A proper training done with a good certification is the only thing it needs.
It is important to note that, under the same field, there are plenty of paths to choose from. Out of all those career paths, which one should you choose? Which is the best Cybersecurity Certification?

Here are a few career paths and jobs to consider in cybersecurity in 2024.
Entry-Level Cybersecurity Jobs:
This career path is for those who have considered beginning their career in the field of cybersecurity. For beginners with no experience, this would be the best place to start their career. All one would need is a good certification to get started.
1. Incident Responder
The role includes tasks like automation testing and conducting system analysis, which helps in identifying the sources of potential breaches.
This is a high-pressure role that also requires a productive and focused mind to analyze the data and communicate across departments. The role is to create and manage comprehensive reports and communicate with individuals from non-technical backgrounds.
2. Security Auditor
Auditing in cybersecurity can offer great opportunities for career growth. The role of the security auditor in cybersecurity is to compile all the reports provided. With the data provided, verification of security and system safety are performed.
This position necessitates the ability to detect any internal system vulnerabilities. The role is to perform multiple penetration tests and to communicate between departments.
Mid-Level Cybersecurity Jobs:
Most working professionals, just after 2-4 years of experience as a security analyst, try to move up to mid-level roles. These job roles are more strategic than the entry-level job roles, but these roles necessarily do not include the leadership positions.
1. Penetration Tester
Key skills expected for this role include:
- Programming skills in Python, Java.
- Network related protocols like HTTPS.
- Vulnerability Assessment and Penetration Testing (VASP)
Certification that helps
2. Forensics Analyst
The role of Forensics Analyst is to investigate digital evidences to solve a crime. They mend all the necessary data to investigate and determine how the breaching happened.
Expected Key skills:
- Assess new tools to identify security vulnerabilities.
- Developing digital forensics based practices
- Perform forensic tasks to detect indicators
Certification that helps
- Certified Forensic Computer Examiner
- Certified Computer Examiner
Senior-level Cybersecurity Jobs:
Senior-level jobs such as Chief Information Security Officer help lead the industry by setting standards for the industry. Hence, these roles involve strategic thinking and futuristic approaches for technical advancements.
1. CISO
The role is to secure every necessary piece of data belonging to the organization. Since organizations collect massive amounts of users' data, privacy and security become more and more crucial.
Key skills expected for the role of Chief Information Security Officer:
- 10+ years of experience in risk management
- Bachelor’s degree in information security
- Knowledge of security frameworks
Certifications considered necessary:
- Certified Information Systems Security Professional (CISSP)
- Certified Information Security Manager (CISM)
- Certified Information Systems Auditor (CISA)
2. CIO
The role of Chief Information Officer does not necessarily come from a cybersecurity background. As the amount of data being collected and used increased, enterprises began to hire leaders from the information and data sectors. Thus, CIOs are not technically part of the field of cybersecurity.
Skills and experience expected:
- A Bachelor's degree in information technology or computer science
- 15+ years of experience, including at least 2-3 years in a senior leadership position
- Capability to work effectively with the CDO and CISO
- Knowledge of cloud technologies
- Keen interest in developing data technologies
Job scope
On the basis of current cybersecurity methodologies, the scope in the field of data analysis and security would only expand. The scope of cybersecurity jobs for professionals is rising.
To create and implement an initiative to develop security systems for organizations, they stay updated on the latest technologies and trends.
According to the Data Security Council of India (DSCI), cybersecurity businesses employed around 1.30–2 lakh workers in 2020, compared to 1.10 lakh in 2019.
According to projections, the cybersecurity market will hire approximately 10 lakh more professionals by 2025.
Conclusion
Cybersecurity is one of these extremely lucrative career paths to pursue.
A cybersecurity career path can be a good place to start if you want to build a strong career base in the field of security and risk analysis. This helps you gain good experience in the field.
By mastering the necessary skills, acquiring more experience would only become easier for any individual aiming for senior-level job roles.
Given the recent market trends, the increased demand for security analysis indicates that the role of cybersecurity professionals will not be a problem for the foreseeable future.
This article details the necessary skills that need to be mastered for the designated job role. This helps you comprehend what must be done to start your career.
The mentioned certifications assist you in mapping your skills to the career path you desire.
To become a certified Security Manager, enroll now to Sprintzeal’s CISM Certification Training and get certified as Certified Information Security Manager.
Related courses to checkout:
CISSP Certification Training Course
CISA Certification Training Course
To explore more courses, consider visiting Sprintzeal’s All Courses page.
Subscribe to our Newsletters
Popular Programs
CISSP® - Certified Information System Security Professional
Live Virtual Training
- 4.8 (964 + Ratings)
- 61k + Learners
CISA® - Certified Information System Auditor
Live Virtual Training
- 4.9 (426 + Ratings)
- 43k + Learners
CISM® - Certified Information Security Manager
Live Virtual Training
- 5 (200 + Ratings)
- 7k + Learners
CCSP® - Certified Cloud Security Professional
Live Virtual Training
- 4.7 (964 + Ratings)
- 69k + Learners
Trending Posts
Mitigate the Cyber-Attack Risks with Best Cyber Security Protocols
Last updated on Nov 14 2023
Top Cybersecurity Software Tools In 2024
Last updated on Jan 22 2024
Fundamentals of Risk-Based Auditing: A Strategic Framework
Last updated on Dec 5 2023
List of Top 10 Cybersecurity Careers in 2024
Last updated on Aug 22 2023
Top 10 Network Scanning Tools of 2025
Last updated on Mar 10 2025
Data loss Prevention in Cyber Security Explained
Last updated on Jun 9 2023
Categories
- Agile Management 55
- AI and Machine Learning 44
- Big Data 53
- Business Management 54
- Cloud Computing 44
- Digital Marketing 57
- Information Security 8
- IT Hardware and Networking 17
- IT Security 103
- IT Service Management 29
- Leadership and Management 1
- Microsoft Program 2
- Other 46
- Programming Language 31
- Project Management 162
- Quality Management 75
- Risk Management 8
- Workplace Skill Building 3
Trending Now
Which Certification is best for Cybersecurity?
ebookTop 5 Compelling Reasons To Get A Cyber Security Certification
ebookHow to Become IT Security Expert with CISSP Certification
ebookTop 20 Reasons You Should Get a CISSP Certification
ebookCISM certification cost and career benefits
ebookWhat is CISSP? – Everything about CISSP Certification Explained
ebookPass CISSP Exam - How to Clear CISSP Exam in First Attempt 2024 (UPDATED)
ebookCISSP Certification – Top 25 Career Benefits in 2024
ebookCybersecurity – Everything You Need to Know About it
ebookCybersecurity Strategy: Building a Strong Defense for Business
ebookCyber Attack Statistics and Trends to Know in 2024
ebookUpdated Google Certification Training Course list 2024
ArticleWhich Cybersecurity Certification Should I Get First?
ebookCysa+ certification – Should you get it?
ebookList of Top Security Certifications
ArticleEasiest Security Certification to Get
ebookCybersecurity Fundamentals Explained
ebookISACA Certifications List 2024
ebookCareer Benefits of CISM Certification in 2024
ArticleList of Top Information Security Certifications in 2024
ebookCISM certification cost details
ArticleSafeguarding Digital Domain: 10 Most Common Cybercrimes
ebookMitigate the Cyber-Attack Risks with Best Cyber Security Protocols
ebookCybersecurity Interview Questions and Answers 2024
ebookData Leak - What is it, Prevention and Solutions
ebookTop Cybersecurity Software Tools In 2024
ebookWhat is Cryptography - A Comprehensive Guide
ebookInformation Security Analyst - Career, Job Role, and Top Certifications
ebookCyber Security Analyst - How to Become, Job Demand and Top Certifications
ebookIBM Data Breach: Is IBM Really Breach-Proof?
ArticleWhat is the Department of Defense (DoD) Directive 8140
ebookInformation Assurance Model in Cybersecurity
ebookWhat is Data Security - Types, Strategy, Compliance and Regulations
ebookData loss Prevention in Cyber Security Explained
ebookCybersecurity Controls Explained in Detail
ebookCybersecurity Framework - A Complete Guide
ebookCybersecurity Career Paths Guide
ebookFuture of Cybersecurity - Trends and Scope
ebookCyber Security Careers and Outlook - 2024 Guide
ebook5 Cybersecurity Predictions in 2024 - Trends and Challenges
ebookEthical Hacking Career: A Career Guide for Ethical Hacker
ebookApplication Security: All You Need To Know
ebookCybersecurity Roles - Top Roles and Skills to Consider in 2024
ebookHow to Get Cyber Essentials Certified
ebookTop 10 Cyber Security Threats and How to Prevent Them
ebookTop 10 Network Scanning Tools of 2025
ebookCyber Incident Response Plan: A Comprehensive Guide
ebookInformation Assurance Careers - Exploring Career Paths
ebookCybersecurity Mesh Architecture: What It Is and How to Build It
ebookWhat is Threat Modeling? Methodologies, Types, and Steps
ebookWhat is Digital Forensics? Types, Process & Challenges
ebookRecent Cyber Attacks & Data Breaches in 2024
ebookHow to Become an Information Security Analyst Salary, Skills, and More
ArticleList of Top Department of Defense (DoD) Approved 8570 Certification Courses
ebookTop 5 Ransomware Attacks to Watch Out for in 2024
ebookJob Prospects for DoD Certified Professionals: A Pathway to Success in cybersecurity
ebook10 Biggest Data Breaches of the 21st Century
ebookWhat is a Cybersecurity Incident?-Types, Impact, Response Process and More
ebookCyber Security Planning - A Detailed Guide for Risk Mitigation
ebookWhat is Cybercrime? Exploring Types, Examples, and Prevention
ebookCybercrime Impacts On Business: 6 Major Effects
ebook5 Types of Cyber Attacks You Should Be Aware of in 2024
ebookCloud Cyber Attacks: Causes, Types, Prevention and Protection
ebookCloud Malware: Types of Attacks and Security Measure
ebookList Of Top Cybersecurity Threats In 2024
ebookRisk-based Audit Planning Guide for Beginners
ebookDemystifying Cloud-Based Cyber Attacks: A Comprehensive Guide
ebookPrevent Cyber Attacks: Strategies to Protect Your Digital Assets
ebookList of Top 10 Cybersecurity Careers in 2024
ebookTop 20 Cybersecurity Trends to Watch Out for in 2024
ArticleHow to Become Cybersecurity Engineer
ArticleUnderstanding Risk assessment in audit planning
ArticleFundamentals of Risk-Based Auditing: A Strategic Framework
ArticleTop 8 Types of Cybersecurity Jobs and Salary Insights
ArticleA Comprehensive Guide to Building Risk-Based Internal Audit Plan
ArticleRisk-Based Internal Auditing Approaches: 7 Steps to Explore
ArticleCompTIA Security+ 601 vs. 701: Understanding Key Differences
ArticleWhy and How to Perform a Risk-Based Internal Audit
ArticleRisk-Based Auditing Techniques Explained
ebookEthical Hacking Tools: Best Ones for Cybersecurity in 2025
ArticleEvolving Cyber Threats and Vulnerabilities in Cybersecurity Risk Management
ArticleWhat Is Secure Access Service Edge (SASE)?
ArticleHow to Stay Cyber-Secure in Work and Personal Life (Tips and Practices)
ArticleTarget Cyber Attack: Key Lessons from the 2013 Data Breach
ArticleLinkedIn User Data Protection Explained
ArticleCanva Data Breach: Best Lessons for Users and Businesses
ArticleHow Did Capital One Respond to Their Major Cyber Incident?
ArticleWhat Innovative Measures Did Reddit Take to Protect User Data?
ArticleHow Does Slack Respond to Security Challenges?
ArticleTwitch Data Breach: Response, Changes, and Key Takeaways
ArticleGuess What Google Did When a Employee Breached Their Firmware
ArticleWhat Happened When Cisco Faced a Cyber Incident?
ArticleWhat Sony Did to Rebuild Trust After a Major Cyberattack
ArticleHow to Handle a Data Breach? Learn from Microsoft!
ArticleCybersecurity Mesh: A New Approach for Security Design
ArticleHow Target Turned a Cyber Crisis into a Lesson for All
ArticleDropbox Data Breach: What Companies Can Learn from It
ArticleHow JPMorgan Chase Strengthened Security After Facing Cyber Threats
ArticleThe Future of Online Security: Trends to Watch in 2025
ArticleLatest Trends in CyberSecurity
ArticleTop 12 Cyber Security Apprenticeships with High Earning Potential in 2025
ArticleEnhancing Safety and Competence in Today's Workplace
Article
















