DevOps vs DevSecOps: Benefits, Challenges, and Comparison
-
 By Arya Karn
By Arya Karn - Published on Jan 21 2026
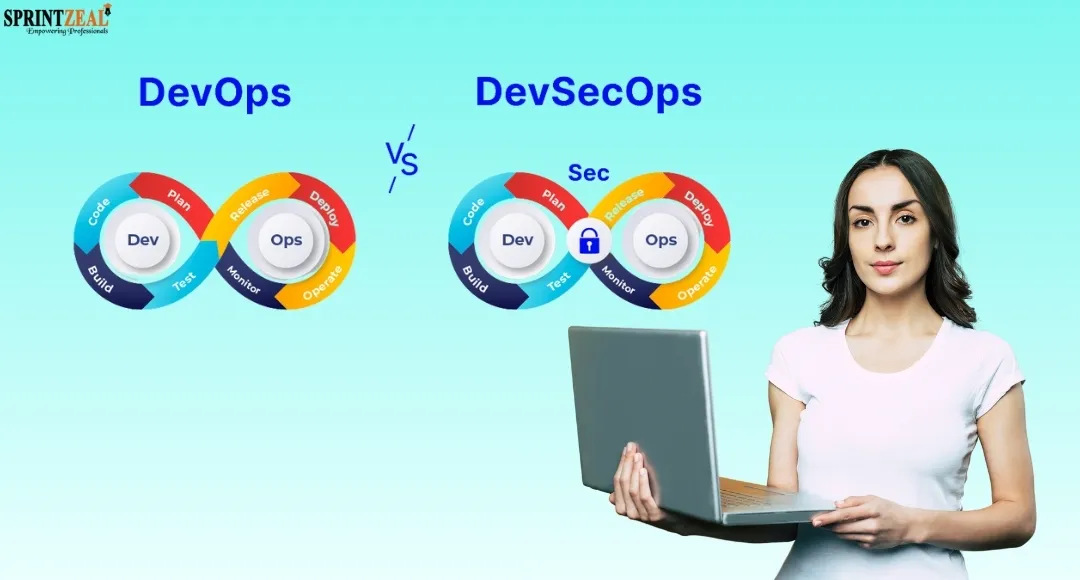
Devops or Devsecops sounds similar right? What do you think? Are they the same or different? Let's burst the bubble; this blog will provide you with a thorough understanding of both processes. Do you know that the majority of companies utilize DevOps and DevSecOps for the fast and safe writing and keeping of their code, there are still some that can't figure out the difference between DevSecOps and DevOps. Both the models are close and have a lot of common things, but they are different. In order to make a suitable decision, it is crucial to weigh the pros and cons of both DevOps and DevSecOps first.
Table of Contents
- What is DevOps?
- What is DevSecOps?
- DevOps vs DevSecOps Overview
- Similarities between DevOps and DevSecOps
- DevOps and DevSecOps: Best Practices
- Which One to Choose: DevOps or DevSecOps?
- DevOps vs DevSecOps Tools
- How to move from DevOps → DevSecOps
- Conclusion
- FAQ's on DevOps vs DevSecOps
What is DevOps?
DevOps is a collaborative approach that unites development (Dev) and operations (Ops) teams with the overall aim to reduce the time of the software development lifecycle, raise the product quality, and have the new features delivered faster. DevOps, instead of separate departments working in isolation, brings teams to work together through the shared standards of ownership, automation, and continuous improvement. This method concentrates on the creation of a culture that ensures software delivery is done in a quick, secure, and reliable manner.
Before moving on if you are preparing for a DevOps interview, we have got the top interview questions asked at one stop.
Core Principles of DevOps
- Collaboration & Shared Responsibility
- Collaboration & Shared Responsibility helps interaction between developers, testers, and IT operations.
- Everyone has one and the same goal: to deliver software that is fast, stable, and secure.
- Automation
- Automation is a feature that, using a set of predetermined routines (tests, builds, installs, monitors, and so on) executes the whole or a part of the task.
- Avoids human mistakes and speeds up release cycles.
- Continuous Integration (CI)
- Continuous Integration (CI) means that developers regularly merge their changes into a shared repository.
- Automated builds and tests facilitate catching errors at an early stage.
- Continuous Delivery & Continuous Deployment (CD)
- It keeps the software unceasingly in a state where it can be deployed.
- Supports on-demand or totally automated release to production.
- Continuous Feedback
- Continuous Feedback makes use of monitoring, logs, and analytics for early issue detection.
- Makes teams revise their processes and code with every release.
Benefits of DevOps
- Due to automation and streamlined workflows, companies can bring their products to market much faster.
- Higher software quality through issue detection at an early stage and continuous testing.
- The consistent releases and stable environments will lead to improved reliability.
- Better team alignment resulting from shared goals and transparent communication.
- The operational costs are lowered by automating and using the resources efficiently.
- Greater innovation results from the fact that teams are less overwhelmed by urgent issues and thus have more time for creating value.
Key Components of DevOps
- CI/CD pipelines
- Version control systems (Git)
- Automated testing frameworks
- Infrastructure as Code (Terraform, Ansible, CloudFormation)
- Containerization (Docker) & Orchestration (Kubernetes)
- Monitoring & observability tools (Grafana, Prometheus, ELK Stack)
- Collaboration platforms (Slack, Jira, Confluence)
How DevOps Works
- Plan: Teams specify requirements, work, and sprint goals.
- Code: Developers produce and commit code to repositories.
- Build: Unattended pipelines take the code, compile it, and run tests.
- Test: Both automated and manual tests serve quality assurance purposes.
- Release: The process of releasing software can be likened to packing the artefacts and getting them ready for deployment.
- Deploy: Through using an automated tool, the code can be transferred to production or staging.
- Monitor: The applications will be under a constant check for their performance, errors, and how the users are impacted.
- Feedback: The insights foster the teams through the next iteration.
If you want to scale up your DevOps journey, go check out this guide.
What is DevSecOps?
DevSecOps is a new software engineering method that involves embedding security measures in each phase of the DevOps life cycle. Instead of considering security as just the last point to be checked, DevSecOps guarantees that developers, security teams, and operations are all on the same page from the outset. The concept of "shifting left with security" allows companies to find security holes quickly, to have security tasks performed by machines, and to be at liberty to deliver safe, compliant, and stable software that can easily be scaled.
Core Principles of DevSecOps
- Co-responsibility for Security
No longer is it effective to assignsolitarily to a team the responsibility for security. Security is a shared responsibility among developers, operations, and the security team.
- Automation
Automation is a key factor in speeding up the time from code to production and reducing the amount of manual effort required through automated tools for such tasks as code scanning, container security, vulnerability detection, and compliance validation.
- Continuous Integration/Continuous Delivery (CI/CD)
Security efforts can all occur without interruption in each CI/CD pipeline. By implementing SAST, SCA, secrets scanning, and IaC, developers can ensure that their code has been secured prior to its release.
- Continuous Monitoring/Feedback
Real-time monitoring allows you to quickly identify any abnormal events, security breaches or misconfigured systems. Continuous feedback loops from teams help ensure that security practices are continuously improving.
- Shift Left/Shift Right Security
The model of shift left indicates that security should be built into the code when it is written and built. Conversely, shift right security involves securing running applications and responding to any identified threats after deployment.
Benefits of DevSecOps
Early vulnerability detection reduces the cost of fixing the issues. The quality of software becomes better through automated and standard security checks being established. The speed of delivery cycles can be increased without security being compromised. Compliance with such frameworks as PCI DSS, HIPAA, and GDPR will be enhanced. The risk of breaches, misconfigurations, and downtime will be lowered. The level of teamwork will be raised as there will be a flow of work that is common to all and which they will also be equally accountable for.
Key Components of DevSecOps
- SAST (Static Application Security Testing)
- SCA (Software Composition Analysis)
- DAST (Dynamic Application Security Testing)
- Container & registry scanning (Docker security)
- Infrastructure as Code (IaC) security tools
- Secrets management (Vault, KMS)
- Runtime protection (WAF, RASP, SIEM, SOAR)
- Compliance-as-code policies
- Monitoring & observability dashboards
How DevSecOps Works
The DevSecOps lifecycle is a set of processes that aims to integrate security in every phase of software delivery through a continuous and seamless flow. The first step is planning, when teams outline security requirements, threat models, and compliance needs right from the start. While coding, developers create secure code and comply with pre-commit checks that attempt to find the issues locally before going to the repository. After code is pushed, the build phase leads to CI pipelines that are automatically triggered to run SAST, SCA, and Infrastructure-as-Code scans so that any security vulnerabilities or misconfigurations may be detected.
Test stage happens next where DAST tools, penetration testing, and policy validations are carried out to ensure that the application remains secure under given real-world scenarios. During the release stage, signatures and verifications are done on artefacts to establish trustworthiness and guard against tampering. Deployment-step relies upon fully automated and security-aware methods along with container and cloud policies so as to assure production is the place where only trusted components are allowed to go.
Afterward, continuous monitoring is there to perform log, metric, threat, and anomaly analysis for always strong runtime protection. Last but not least, feedback loops convert these monitoring results into security-enhancement measures that give teams the possibility to not only tighten security controls but also improve future product versions.
DevOps vs DevSecOps Overview
DevOps is all about speed, automation, and continuous delivery by merging the development and operations teams for a quicker and more stable release via CI/CD pipelines and tools like Git, Jenkins, Docker, Kubernetes, and Terraform. DevSecOps takes this change one step further by including security from the very beginning and therefore, no security issue is left unnoticed, e.g., with automated checks like SAST, SCA, DAST, and threat modelling while still keeping the velocity.
-
Core Teams and Goals
The core teams of DevOps are the development and operations, and the main goal is the release of the software with high stability confirmed via functional and performance testing. DevSecOps is a concept that includes not only development, security, and operations but also a common goal of releasing software faster and at the same time continuous security improvements through security tests conducted at each stage.
-
Pipeline and Security Practices
Security in DevOps is a late-stage or post-deployment activity accompanied by reactive risk management and compliance that are outside of pipelines. DevSecOps makes a change by moving security to the left side, i.e., from the planning to the deployment stage and thus, security is ensured by taking the most proactive measures, using IaC scanners, WAF, SIEM, and compliance-as-code to catch vulnerabilities early.
-
Culture and Outcomes
DevOps is a culture where the different teams work together, share the ownership, and thereby accelerate the whole deployment cycle. DevSecOps is a culture where security is the responsibility of all and that leads to the fast release cycles with the risk level being also low thanks to continuous monitoring and automated compliance
Similarities between DevOps and DevSecOps
Though DevOps and DevSecOps may be twins in many ways, they still have different emphases. Where one concentrates on speed and collaboration, the other, security is integrated into the same workflow; however, these two concepts share a lot of foundational similarities and thus, are closely linked in modern software engineering. Firstly, both these paradigms were conceived to cater to the problems of conventional development, save on delivery time, and grant powers to the team to craft quality software without the trouble of unnecessary postponements. The major correspondences between these were explained and enumerated as follows:
-
Shared Goal of Faster, High-Quality Software Delivery
The main objectives of DevOps as well as DevSecOps are to simplify the software development lifecycle and to serve customers with their orders in a speedy and ever-reliable way. Succeeding are the obstacles of silos, bottlenecks, and release cycles; thus, the practice becomes a mainstay in a development environment which brings robust applications fast as well as steady to the market.
-
Culture of Collaboration and Transparency
A collaborative culture is the core of the two named techniques. DevOps encourages cooperation between development and operations, whereas DevSecOps facilitates this collaboration further by bringing security teams on board. The principles reflected in the models include communication, openness, and joint responsibility, which form the groundwork for abandoning the delivery method known as "throw it over the wall".
-
Strong Dependence on Automation
Both methodologies dot the i's and cross the t's with automation in their strategies. 'To automate' is the word in wholly describing DevOps scenarios such as CI/CD, testing, deployment, and monitoring. On the other hand, DevSecOps leverages the same processes but attaches automated security checks (SAST, SCA, policy validation, etc.). The point of automation is to lessen the manual efforts part of the job, heighten the chances of success, and keep the standards.
-
Continuous and Iterative Approach
For the reason of striving for continuous improvement, both DevOps and DevSecOps have embraced this idea. Continuous integration, continuous testing, continuous monitoring, and feedback loops are implemented as solutions to issues of late detection and hence, refining upcoming versions. DevSecOps just simply incorporates the same concept for security.
-
Use of Modern Toolchains and Cloud-Native Practices
Both DevOps and DevSecOps lean on contemporary tools such as containers, microservices, orchestration systems, CI/CD platforms, and monitoring dashboards. SecOps does it in the same way but with the addition of security scanners, compliance tools, and runtime protection systems.
-
Focus on Reducing Risks and Failures
Both DevOps and DevSecOps work to lessen the risks of the operation, downtime, and deployment failures. The orchestration of the mitigations is done through infrastructure automation and observability in the case of DevOps, while to empower the overall resilience, DevOps adds vulnerability detection and threat mitigation to it.
-
Alignment With Agile Methodologies
Both models are in line with the principles of Agile by facilitating iterative development, rapid releases, and ongoing collaboration. The only difference is that in DevSecOps security becomes a part of Agile sprints and ceremonies
DevOps and DevSecOps: Best Practices
-
Build Unified Teams
Encourage the collaboration between development, operations, and security teams so that they can agree on shared goals, co-operate in breaking down silos for seamless workflows and generate mutual trust. Combining these teams in this way leads to faster, secure software delivery while also ensuring that the shared accountability is there from the very beginning.
-
Educate and Train
Provide training to the teams on DevOps and DevSecOps principles, and then let them see the value of these principles by the increased efficiency, innovation, and security posture that are the result of them. The process of sharing knowledge leads to the formation of a common language; therefore, resistance is lowered, and the teams become empowered in the proactive management of vulnerabilities.
-
Automate Pipelines
Use CI/CD and security testing tools such as SAST and DAST to perform the operations automatically; thus, the number of errors is lowered, the releases are sped up but the quality is not compromised. Automation is a way of ensuring that the work is done consistently and that there are checks done; at the same time, it allows the teams to be free for other tasks of higher value.
-
Shift Security Left
The security measures must be integrated in every development stage – planning, coding and deployment – so security vulnerabilities can be detected early and the costs for fixing them will be lower. This proactive "shift left" strategy leads to an increase in the overall software resilience.
-
Enable Version Control
Implement strong tools such as Git for the purposes of change tracking, collaboration facilitation, and quick rollback in case of problems. Centralised control is the one that supports branching strategies, which are used for maintaining code integrity across teams.
-
Implement Feedback Loops
Put in place the mechanisms for continuous feedback that will lead to process refinement, faster issue detection, and iterative improvements in development and security. Short loops are beneficial as they encourage transparency as well as rapid adaptation to the changing characteristics of the threats.
-
Monitor Post-Deployment
Performance of the application as well as security-related metrics after the deployment should be followed with the help of tools such as SIEM in order to obtain real-time insights and make optimisations. Continuous monitoring is an assurance of a sustained user experience as well as compliance in production environments.
To know in detail about the best DevOps practices, check out this amazing blog.
Which One to Choose: DevOps or DevSecOps?
1. DevOps — When to Choose It
- It is an extremely good fit if your chief aims were to achieve speed, automatize and have quicker release cycles.
- This model is best suited for teams whose main focus is on CI/CD pipelines, rapid iterations, and frequent deployments.
- It is advised to use this approach when security is taken care of by a separate team or through occasional audits.
- Such a model is appropriate for startups or agile teams where the time-to-market is more of a priority than strict governance.
- On the other hand, it is at its best when your product is at a lower risk of security or compliance.
- DevSecOps — When to Choose It
- This is an absolute must for organizations placing security as a top priority at every developmental stage.
- These are industries such as finance, healthcare, BFSI, enterprise SaaS, or the government, where this is mandatory.
- You will find it most beneficial when you rely on such security measures internally and also use tools such as SAST, DAST, container scanning, and policy-as-code.
- Good as it is, it enables the discovery of security gaps at an early stage thus lowering the cost, delay, and risk factors that arise after production.
- Apart from compliance, it is best suited for teams with a risk management focus and those who handle sensitive data.
- How to Decide Between the Two
The right choice for a DevOps approach would be if your main emphasis was on:
- Faster delivery
- Automation
- Developer–Ops collaboration
- Short development cycles
On the other hand, if security was your main concern, then DevSecOps would be your choice, and the list of priorities would be as follows:
- Continuous security
- Compliance and governance
- Secure-by-design development
- Reducing vulnerabilities early
DevOps vs DevSecOps Tools
1. DevOps Tools - Focused on Speed, Automation & Delivery
CI/CD & Automation Tools
- Jenkins – Known for pipeline automation.
- GitLab CI/CD – Single platform for version control and CI/CD.
- GitHub Actions – Automation with easy, YAML-based workflows.
- Azure DevOps Pipelines – CI/CD pipelines at a scalable enterprise level.
Containerization & Orchestration
- Docker – The most widely used container platform.
- Kubernetes – A tool that provides both orchestration and scalability of applications.
- Helm – Kubernetes apps packaging management.
Infrastructure as Code (IaC)
- Terraform – IaC that is not tied to any cloud provider.
- AWS CloudFormation – IaC that is native to AWS.
- Ansible – Configuration automation.
Monitoring & Observability
- Prometheus – Metrics collection.
- Grafana – Dashboards and visualization.
- ELK Stack (Elasticsearch, Logstash, Kibana) – Centralized logging
2. DevSecOps Tools Focused on Security, Compliance, and Risk Prevention
Code & Application Security
SAST Tools:
- SonarQube
- Checkmarx
- Fortify
DAST Tools:
- OWASP ZAP
- Burp Suite
Container & Cloud Security
- Aqua Security – Container, kubernetes & cloud workload protection
- Prisma Cloud – Cloud security posture + workload scanning.
- Anchore – Container image scanning.
- Trivy – Lightweight vulnerability scanner.
Secrets & Identity Management
- HashiCorp Vault – Secrets management.
- AWS Secrets Manager – Cloud-native secret storage.
- Azure Key Vault – Centralized key & secret management
Compliance & Policy Automation
- OPA (Open Policy Agent) – Policy-as-code across systems.
- Snyk – Dependency scanning + license compliance.
- Kubescape – Kubernetes security & compliance checks.
Not only there are many other tools, but here we have also created a list of DevOps tools do follow.
How to move from DevOps → DevSecOps
1. Make Security a Shared Responsibility
Secure integration roles should be a part of daily DevOps routines. Developers should be trained in secure coding and security concepts.
- Embed Security Into Every CI/CD Stage
- Plan → Threat modeling
- Code → Dependency scanning
- Build → Image & package checks
- Test → SAST/DAST/SCA
- Deploy → Policy-as-code, secrets scanning
- Monitor → Continuous threat detection
- Automate All Security Checks
- Add scans to pipelines (SAST, DAST, IaC).
- Automatically block deployments that have critical vulnerabilities.
- Let risky commits trigger real-time alerting.
- Strengthen Secrets & Access Control
- Implement Vault/Azure/AWS secret managers.
- Least-privilege and MFA should be enforced.
- Secret rotation should be automated.
- Shift Left with Early Security Testing
- Code should be scanned at commit time
- Vulnerabilities should be fixed prior to the integration stage.
- Lightweight, fast scanners should be used for dev workflows.
- Secure Cloud, Containers & APIs
- Enforce Kubernetes policies (OPA, Kyverno).
- Use container scanning (Trivy, Anchore).
- Apply CSPM tools for cloud misconfigs.
- Track Metrics & Improve Continuously
- MTTR for vulnerabilities
- % of builds passing security checks
- Compliance score
- Zero-trust alignmen
Conclusion
DevSecOps is the next step for companies that want fast software releases and strong security. Short release cycles plus cloud systems now demand that security checks begin at the first design stage, not later. To succeed, every role must treat security as part of daily work - automation, the right tools and clear metrics support this new habit.
The best payoff comes from a narrow start - add dependency scans but also secure templates for infrastructure. After those run smoothly, expand to always on monitoring, rules written as code and alerts that reach coders within their normal tools. A maturity map lets teams pick early projects, watch security KPIs as well as avoid buying duplicate tools.
People who want solid DevOps skills and a later move to DevSecOps gain speed from formal training that covers tools, processes or long-term upkeep.
FAQ's on DevOps vs DevSecOps
1. Is DevSecOps only DevOps plus security?
No. It moves every security task into the same timeline as design, coding, testing and release.
2. Must I create a new team?
No. Operators also security staff share the load - a few security champions inside each squad guide the rest.
3. Which tools are required?
DevOps needs CI/CD, containers and monitors - devSecOps adds static code scans, dependency checks, dynamic tests, infrastructure scans and safe storage for secrets.
4.Does DevSecOps delay releases?
Done well, it shortens them - early fixes remove later rework.
5. Which is better: DevOps or DevSecOps?
For modern cloud-native applications, DevSecOps is the smarter evolution of DevOps.
Subscribe to our Newsletters
Popular Programs
AWS Certified Solution Architect Professional
Live Virtual Training
- 4.9 (300 + Ratings)
- 28k + Learners
AWS Certified DevOps Engineer Certification Training
Live Virtual Training
- 4.7 (400 + Ratings)
- 65k + Learners
Microsoft Azure Administrator Associate AZ-104
Live Virtual Training
- 4.8 (560 + Ratings)
- 14k + Learners
Microsoft Azure Infrastructure Solutions (AZ-305)
Live Virtual Training
- 4.4 (560 + Ratings)
- 47k + Learners
Trending Posts
Client Server Model—Everything You Should Know About
Last updated on Dec 17 2025
Cloud Computing and Fog Computing - Key Differences and Advantages
Last updated on Jun 19 2023
AWS Architect Interview Questions - Best of 2026
Last updated on Feb 24 2023
Azure Vs Aws - Which Technology Is Better
Last updated on Jul 30 2024
Must-Have AWS Certifications for Developers in 2026
Last updated on Jan 2 2025
Continuous Deployment Explained
Last updated on Jul 14 2023
Categories
- Other 73
- Agile Management 49
- Cloud Computing 58
- Project Management 174
- Data Science 68
- Business Management 88
- Digital Marketing 82
- IT Service Management 29
- Programming Language 60
- AI and Machine Learning 86
- IT Security 113
- Quality Management 78
- IT Hardware and Networking 26
- Microsoft Program 5
- Workplace Skill Building 15
- Risk Management 9
- Information Security 8
- Leadership and Management 9
- Corporate Training and Development 1
Trending Now
Azure Vs Aws - Which Technology Is Better
ebookThe Impact of Internet of things on Marketing
ebookAWS Lambda - An Essential Guide for Beginners
ebookCareer in Cloud Computing or Cyber Security
ebookImpact of AWS Certification On Cloud Computing Jobs
ebookAmazon Certifications: List of Top AWS certifications in 2026
ebookAWS Interview Questions and Answers 2026
ebookAmazon Software Development Manager Interview Questions and Answers 2026
ebookAWS Architect Interview Questions - Best of 2026
ebookHow to Become a Cloud Architect - Career, Demand and Certifications
ebookWhat is Cloud Computing? - Fundamentals of Cloud Computing
ebookAWS Solutions Architect Salary in 2026
ebookAmazon EC2 - Introduction, Types, Cost and Features
ebookAWS Opsworks - An Overview
ebookAzure Pipeline Creation and Maintenance
ebookCI CD Tools List - Best of 2026
ebookTrends Shaping the Future of Cloud Computing
ebookContinuous Deployment Explained
ebookDevOps Career Path – A Comprehensive Guide for 2026
ebookTop Kubernetes Tools in 2026
ArticleBenefits of Cloud Computing in 2026
ebookJenkins Interview Questions and Answers (UPDATED 2026)
ArticleA Step-by-Step Guide to Git
ArticleScalability in Cloud Computing Explained
ebookIoT Security Challenges and Best Practices-An Overview
ebookHow to Learn Cloud Computing in 2026 - A Brief Guide
ArticleCloud Engineer Roles and Responsibilities: A complete Guide
ebookTypes of Cloud Computing Explained
ArticleCloud Engineer Salary - For Freshers and Experienced in 2026
ArticleEssential Cybersecurity Concepts for beginners
ebookWhat is a Cloud Service - A Beginner's Guide
ebookTop 3 Cloud Computing Service Models: SaaS | PaaS | IaaS
ArticleWhat is Private Cloud? - Definition, Types, Examples, and Best Practices
ebookWhat Is Public Cloud? Everything You Need to Know About it
ArticleTop 15 Private Cloud Providers Dominating 2026
ebookWhat Is a Hybrid Cloud? - A Comprehensive Guide
ebookCloud Computing and Fog Computing - Key Differences and Advantages
ebookAzure Architecture - Detailed Explanation
ArticleMost Popular Applications of Cloud Computing – Some Will Shock You
ArticleTips and Best Practices for Data Breaches in Cloud Computing
ArticleWhat Is Edge Computing? Types, Applications, and the Future
ArticleMust-Have AWS Certifications for Developers in 2026
ArticleSalesforce Customer Relationship Management and its Solutions
ArticleCutting-Edge Technology of Google Cloud
ArticleSpotify Cloud: Powering Music Streaming Worldwide
ArticlePublic Cloud Security Checklist for Enterprises
Article12 Best Managed WordPress Hosting Services in 2026
ArticleLatest Azure Interview Questions for 2026
ArticleTop Coding Interview Questions in 2026
ArticleLatest Cloud Computing Interview Questions 2026
ArticleSafe file sharing for teams: simple rules that work
ArticleMy learning path to become an AWS Solutions Architect
ArticleClient Server Model—Everything You Should Know About
ArticleWhat Is Microsoft Azure? A Complete Cloud Computing Guide for 2026
ArticleDocker Tutorial for Beginners: Containers, Images & Compose
ArticleGit Merge vs Rebase: Differences, Pros, Cons, and When to Use Each
ArticleThe Invisible Infrastructure Powering Tomorrow’s Apps
Article








.png)








